UNIVERSITY OF CAMBRIDGE INTERNATIONAL EXAMINATIONS
General Certificate of Education Ordinary Level
COMPUTER STUDIES 7010/01
Paper 1
May/June 2004
2 hours 30 minutes
General comments about this paper
These comments are based on
Interviews with students who sat the paper
Questions answered in class time by current o-level students
Completion of the paper by myself.
The level of language used is suitable for students in Brunei. Questions are written in a relatively simple form. However, having quizzed students who sat the test and also having answered all the questions myself I did find that students had trouble understanding what was asked in a few instances.
Students will have to be aware that questions related to the data protection act require answers directly related to UK law statutes on this matter. They can not "ad-lib" an answer using common sense. Brunei law is different.
As has been the trend in recent years students are required to answer more questions "further up Blooms taxonomy" than in the past. They must use what knowledge they have to come up with solutions to problems. This is as it should be Computer Studies is about developing student problem solving skills. We should continue to move away from giving students lists of words to remember!
Some questions are open ended. It would be easy for students to lose track of time as they spend more time than necessary talking about the steps in a SDLC. In particular, the questions about system development have a multitude of possible answers. The waterfall model given in most textbooks being one of the methods less favoured these days. I would be interested in how this question was marked!
Some questions appeared simple but were not. In particular the spreadsheet question required that students look very closely at their answers. For example, the first question included formatting features such as Bold, Center and word wrap. At fist glance students missed the word wrap formatting feature. Also the formula in this question makes use of absolute addressing. Again, students did not pick up on this straight away. Our students were most surprised when they actually replicated the spreadsheet question with Excel and found that things were not so simple!
The question about a network for a surgery does not provide very much information upon which to base an answer. Again, there is a multitude of possible answers for this type of question.
Overall, I think students will need to be careful about time when completing this paper. They will need to take care to ensure that they answer questions fully. The questions are generally very fair. It is a good paper.
*** Answers and evaluation ***
Section A
Explain, using examples where appropriate, the meaning of these computer terms.
a. byte
A binary number consisting of 8 binary digits. Information stored in the memory of a computer is stored in bytes.
b. compiler
A compiler is a software program that will create a machine code (executable) version of a high level language (source code) program.
c. handshaking
Different communication devices need to agree on a protocol before they can successfully transmit data to each other. The process of agreeing on a protocol for communication is called handshaking.
d. technical documentation
The documentation that a system administrator or system developer will need if they are to modify an existing system. This might include a data dictionary, process specifications, source code, database schema and other useful information.
e. simulation
An artificial computerized version of a real situation. For example, a flight simulator.
(a) Give one example of wireless technology.
Some LANs now use wireless technology for transmitting data between computers.
(b) Give one benefit and one disadvantage of the use of wireless technology.
Benefit: There is more flexibility about arranging hardware. There is no need to reroute cables when computer hardware is moved from one location to another.
Disadvantage: Cable networks mostly have higher data transfer rates (bandwidth) and are less expensive to install for small networks (such as those we might find in a small office).
(a) State two places where robots are used.
(i) In car manufacturing plants (ii) in places which are dangerous for human beings such as for exploration inside volcanoes
(b) State two benefits of using robots.
(i) They can work twenty four hours per day, seven days per week
(ii) They are able to maintain a constant high level of quality when used in manufacturing operations.
(a) State two effects of a computer virus.
(i) Information stored in a computer system may be altered
(ii) The infected computer is able to transfer the virus to other computers on a network or to any secondary storage media that the computer can access.
(b) State two ways of protecting computers against viruses.
(i) Ensure that users do not transfer data from unknown locations such as dubious websites or open e-mail attachments from unknown persons.
(ii) Ensure that anti virus protection software is installed.
Interfaces enable computer users to interact with the operating system. State three advantages for using a graphical user interface (GUI) for loading programs and files.
(i) It is easier for us to remember what an icon is for than it is to remember text command lines required to load files.
(ii) It is usually faster for the user to click on an icon than to type text into a command line interface
(iii) It is less likely that a user will accidentally do something unintentional when using a GUI. Command line text can have many parameters and it is often important to enter exactly the correct parameters to avoid unintentional actions being carried out.
(a) Name one item used in the home, other than a computer, that contains a microprocessor.
washing machine
(b) For your item named in (a) describe two different tasks that the microprocessor performs.
(i) The processor accepts input from the washing machine control panel. It uses this information to determine the wash program to be used and hence what signals to send to the valves and motors that control the operation of the washing machine.
(ii) The processor receives data from sensors to indicate the water level in the washing machine. If the water reaches a certain height then the computer will send a signal to turn off a valve so that the water stops entering the washing machine.
A programming language has instructions for moving a pen on a piece of paper. Examples are:
FlO Move forward 10cm
B20 Move backwards 20 cm
R90 Turn right 90 degrees
L90 Turn left 90 degrees
Write a set of instructions that would produce the following drawing:
F4 L90 F4 L90 F2 L90 F2 R90 F2 L90 F2 L90
8 A school wants to create its own website to advertise the school.
(a) State the type of software that would be used to create a web
page.
A webpage editor such as Microsoft Frontpage.
(b) State two features of the software used to design web pages.
(i) The webpage editor will automatically translate our page
into HTML.
(ii) The software will make it easy for us to upload our webpage files to a web hosting ISP.
(c) State where the finished website would be stored so that people
surfing the Internet can visit it.
The website would be stored on an internet file server run by an
internet service provider that offers web hosting facilities.
A supermarket uses point of sale (P05) terminals at the checkout for scanning barcodes on the products.
State two items of data that are stored on the barcode.
(i) A code for the company supplying the item
(ii) An item code for the product
(b) Describe how the computer system checks that the barcode has been read correctly.
The computer system will read the barcode check digit. This will be compared to the check digit calculated using the rest of the barcode. If the two digits do not equal each other then the computer system will indicate that the barcode has not been read correctly.
(c) State the type of file access that is used to get the price from the central computer.
We would use random access to get the price form the central computer.
(d) Explain how the system updates the file when an item has been sold.
A field on the central computer database table will contain the "quantity on hand" for all products. The amount in this field will be decreased when an item is sold.
(e) Give two benefits for the supermarket manager of using point of sale (POS) terminals.
(i) The supermarket manager can use the transaction data stored on the central computer to see stock levels. He can reorder stock before running out. In fact the reordering process can be automated using EDI with suppliers, meaning less work for the staff in his supermarket.
(ii) The cashiers using the POS terminals provide a good service to customers. This will attract new customers and encourage return customers. This is a good thing as far as the supermarket manager is concerned.
10 (a) A company has decided to use a computer for stock control. Describe the process of systems analysis from the time the decision was made to proceed with computerisation until final testing.
We would use a system development life cycle approach to produce a system that the user will be happy with.
(i) Problem recognition (requirements analysis). We would need to investigate the current system to see where the problems lie and what processing, data capture and outputs are required.
(ii) We would determine what the objectives of system development are to be. This may mean producing a document called a requirements specification.
(iii) We should then come up with a number of design alternatives that satisfy requirements specification. Theses design alternatives are quite detailed and include hardware specification, scope of the system, software, budget, time and resources required for building the system, a data schema and an estimate of the time for the return on investment.
(iv) We must determine which alternatives are likely to be candidates for development. It is helpful to rank the alternatives so that it is obvious which is the choice that best meets the needs of the business.
(v) The above information is put together nicely in a feasibility report that can be sent to the business along with a recommendation from the systems analyst.
(vi) Given that the business allows development of the stock system we will then need to do a detailed analysis of the stock system to produce a design specification. This will mean creating a data dictionary, process specifications, dataflow diagrams and other diagrams as needed to correctly and accurately describe the specification of a new system.
(vii) Once a design specification exists and this has been tested, then processing software can be created and a database can also be built.
(viii) After programming the new system it will be necessary to carry out testing to ensure that the new system is working. The system will be put in place and might be run in parallel with the old system to ensure that it is working properly.
(ix) Data will need to be converted from the old system to the new system. This might mean using key to disk to populate database tables.
(x) End user acceptance testing will take place. If the system is found to meet or exceed end user expectations as expressed in the requirements specification then the system can be allowed to replace the old system.
10 (b) Give two reasons why it may be necessary to modify this system in the future.
(i) the requirements specification may change requiring maintenance/modification of the new system. Changes may be due to improper understanding in the first place or because users see value in changing the scope of the new system to include new features.
(ii) new technology may offer opportunities for new services to be developed that enhance the information system. The use of electronic data interchange with suppliers is an example of how the stock control system might be enhanced in the future.
11 A family has purchased a computer system with the following specification:
Processor speed 2200 MHz
RAM 512 Megabyte
Hard disk drive 120 Gigabytes
CD ROM
DVD writer
Modem 56k
Monitor 17"
(a) The computer has been purchased for buying goods and services over the Internet. Explain how each of these items of hardware would be used for this purpose.
Hard disk drive - to store programs such as the browser and computer operating system.
RAM to store program instructions and data so that the processor can execute programs.
DVD writer to store downloaded purchases such as software music or movies
Modem to connect the computer to an internet service provider.
(b) State the type of software that is needed for logging onto the Internet and finding websites selling goods and services.
(i) logging on we use a browser to access html pages at a WWW site.
(ii) finding websites we would use a search engine to locate websites for making purchases
(c) State one advantage and one disadvantage for customers of using the Internet for shopping.
(i) advantage we have greater variety and better prices than can be found locally
(ii) disadvantage we must pay for shipping and wait for our purchases to arrive
(d) Describe two effects on society of an increase in the use of the Internet for e-commerce.
(i) People can easily buy things that are not available locally. So they have access to more material goods than in the past.
(ii) People will have to learn to use credit cards and become computer literate to be able to shop online.
12 The following spreadsheet shows the profit or loss on sales at an ice-cream stall during a four week period.
(a) State the format of the data in cell B6.
centred/bold/word wrapped
(b) Write down a formula that could be in cell D7 to calculate the Income for week 1.
=$B$3 * B7 + $B$4 * C7
(c) Describe how the formula in D7 can be copied into the cells D8, D9 and D10.
The formula in D7 can be copied to the clipboard and then the range D8:D10 is highlighted before pasting from the clipboard. Note that this will work properly as long as B3 and B4 are treated as absolute addresses.
(d) Cell F7 contains the function:
=IF(D7> E7, Profit, Loss)
and is copied into cells F8, F9 and FlO. Write down the function that will be in cell FlO.
=IF(D10> E10, Profit, Loss)
(e) State the cells that are needed to create a line graph to show the Income and Expenses for Week 1 to Week 4.
The x-axis data will include the labels in the range A7:A10
There will be two series for the lines in the chart. The series for expenses will be E7:E10. The series for income is set to the range D7:D10.
13 A city uses a computerised traffic control system
(a) State two benefits of using computerised traffic control systems.
Better road traffic flow since the computer can be programmed to minimize the length of time that drivers have to wait at traffic lights.
(b) Describe the input, processing and output from this control system.
Input: A signal from a sensor that can tell if a large piece of metal is above it provides data to the processor of the computer system controlling the traffic lights.
Processing: The computer can determine if people are waiting at a red light or not. If the input from the road sensor indicates that there are cars waiting then the computer can generate a sequence of actions that will eventually change the lights. There is likely to be a feedback loop signal that indicates the current state of all lights in the system. Any unusual feedback (such as no feedback form one light) might indicate that the lights are not working correctly.
Output: The output produced by the computer will be a signal that is used to turn red, orange and green lights on and off. A feedback loop response indicating a fault might trigger a computer program that alerts a traffic controller.
(c) Describe what the traffic control program should do when an emergency
occurs.
A feedback loop response indicating a fault at the intersection control system might trigger a computer program that alerts a road traffic controller (a person) at a central location. This would mean a message is sent either by telephone or radio signal.
14 A surgery uses a star local area network (LAN) to access the Internet (WAN) and to store the patient database.
(a) Give one reason why the surgery has installed a star network rather than a ring network.
A star network topology is a simpler and less expensive configuration than a ring topology. A star network is more susceptible than a ring network to performance degradation as the amount of traffic on the network increases, but this is unlikely to be a serious problem in a surgery environment.
(b) Draw and label the star network used by the surgery.
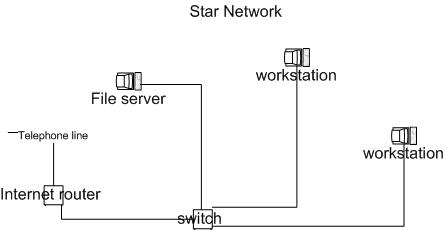
(c) Give two benefits for the surgery of storing the patient database on the LAN.
(i) Information can be accessed quickly and easily from many locations. Information access is more timely and can be provided in the format most suitable for the recipient.
(ii) Data can be analysed for a number of purposes other than simply recording patient case notes. It will be possible to list all patients who have not paid their bills on time simply by generating a report rather than having to go through files manually.
(d) State two data protection rules that the surgery staff must obey.
(i) Patient information can not be released to people who are not allowed to see it. This sensitive information must be protected properly.
(ii) The surgery must provide information to the patient about what they have on their computer about them. The patient has the right to know what information has been recorded.
(e) Describe how the database can be recovered from a system failure.
A disaster recovery plan will be implemented if there is a system failure. The recovery plan is to ensure that the system is up and running again in the shortest possible amount of time. The plan might include identifying the source of the problem and then taking steps to rectify the problem. If mirror sites are used then it might be that the users do not even know that something has broken down since a copy of the database in another location will be used while the problem is sorted out by technicians who monitor the system. In a small business it is likely to have a service contracts that guarantees the "mean time to repair" is less than say 2 hours. Thus hardware can be repaired or replaced quickly. Data can also be recovered using backups.
15 Read this algorithm. The algorithm converts a temperature from degrees Centigrade to degrees Fahrenheit.
(a) Write down the output for each of the following inputs:
(i) 1 output is 33.8
(ii) 5 output is 41
(b) Using pseudocode, or otherwise, write an algorithm that will input the hourly temperatures for one day in Centigrade and print out in Fahrenheit
the maximum temperature
the minimum temperature
the average temperature
for that day.
Input temp
Move temp to max
Move temp to min
Move temp to sum
Move 1 to hour
Do while hour < 24
Input temp
If temp > max then
Move temp to Max
End if
If temp < min then
Move temp to Min
End if
Move hour + 1 to hour
Move sum + temp to sum
End while
Move sum divided by 24 to average
Output max
Output min
Output average
16 A music club keeps a file of members on a computer system. Part of the file is shown in the
following diagram:
(a) State how many fields there are in each record.
6
(b) State the data type that should be used for the CODE data.
Alphanumeric
(c) State two reasons why the data in the SEX field has been coded.
(i) It is easier to enter a single character than a whole word.
(ii) Less memory will be used storing single characters instead of whole words.
(It is less likely that a data entry error will occur if only one character is typed in.)
(d) Which CODE data will be listed if the following search condition is input?
(DATE OF BIRTH< 01/01/87) AND (SEX ="M")
M1057, M1124
(e) Describe how the file can be sorted in ascending order of SURNAME.
We can create a query that includes all the fields in the above table and that will produce a view that displays all records in alphabetical (ascending) order according to surname.